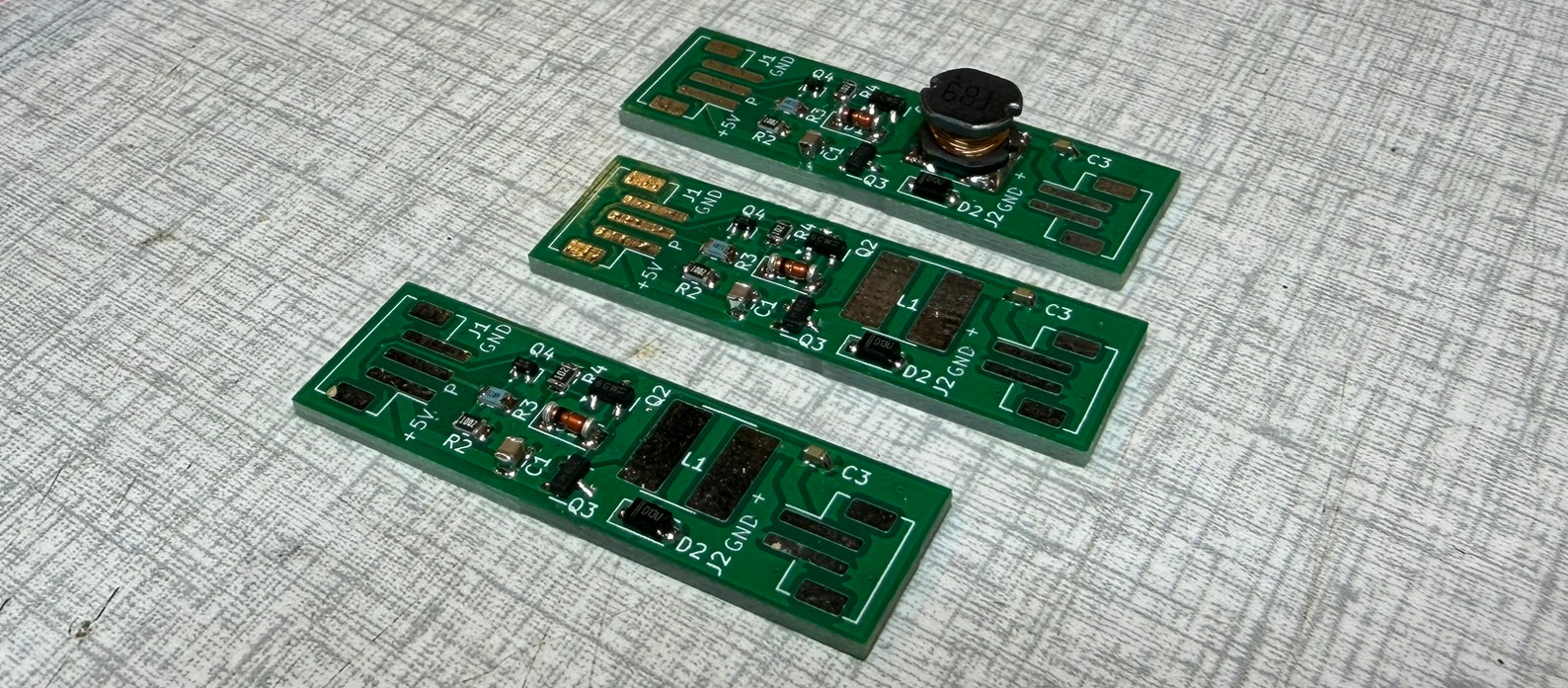
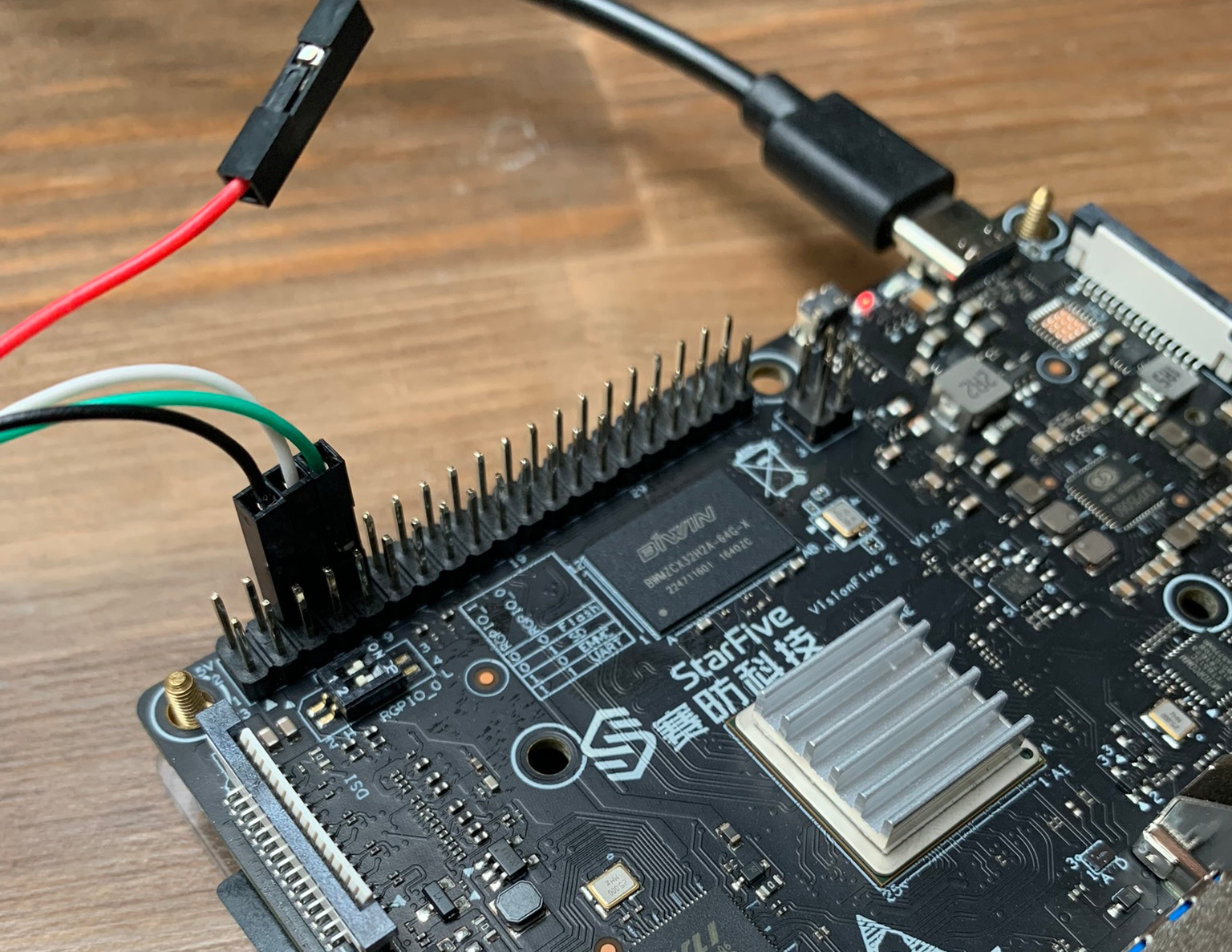
Welcome! Imagine creating a web site to write about projects and findings with the intention of sharing information that others find useful. That is what this is.
Feedback and comments
I value feedback. But in my opinion on-line fora rarely do anything good for soliciting constructive feedback or refining criticism. Therefore, please do send feedback to jakob@unthought.net directly.